Those ‘lovely’ people at Microsoft have been tinkering with the Edge browser. They are keen for us to try it. So keen, that it is being pushed out as a ‘Windows Update’.
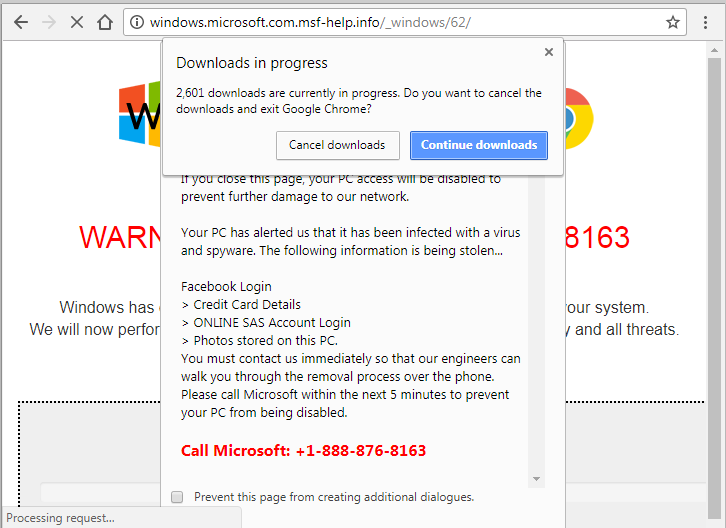
Following a restart of your machine you will be faced with this screen….

From which it is impossible to escape. There is no close button, hitting Escape does nothing and even pulling up the Task Manager with Ctrl + Alt +Del doesn’t give a clue as to how to avoid going through the forced migration process.
Migration is probably the wrong word, it is more like your account is being taken hostage by Edge. By the time you reach this screen it has slurped up a lot of your details from your existing browser (history, favourites, saved card details etc) and is is waiting for you to confirm your acceptance of the migration. It seems impossible to avoid being sucked into ‘new’ Edge; resistance, as they say, is futile!
However, you can sidestep it, if you know how.
How to Avoid Edge
Counter intuitively, you do first have to hit the ‘Get Started’ button. However, unlike a parachute jump without the parachute, this is one adventure where you will live to tell the tale.
After hitting Get Started, it will ask you if you want to import from your existing browser (Chrome, Firefox, Opera, it doesn’t matter, they really, REALLY want you to migrate). Along side this very prominent button, is a much less prominent link that says “Continue Without Importing“. Hit this option.
You will be pestered to change your mind but persist and you can move on and continue with your preferred browser.
Those of you with a long memory may recall when Microsoft were punished (heavily) for making it difficult for Windows users to use any browser other than Internet Explorer. It feels like we have gone full circle!
By all means Microsoft, create new versions of your software. By all means roll it out to user but please don’t force me to use it. I would like to decide for myself. ‘New’ Edge has been getting favourable reviews and I was half tempted to give it a try. Sadly these ‘dirty tricks’ mean that it has been consigned to the same place as the legacy Edge – the bin.




 transactions should have alarm bells ringing loudly. No legitimate fundraising site would ask for payment to be made this way.
transactions should have alarm bells ringing loudly. No legitimate fundraising site would ask for payment to be made this way.





 I’ve been asked this question several times in the last week. When you turn it around and ask the questioner how long they reckon it will take, the answer is usually several hours, if not days.
I’ve been asked this question several times in the last week. When you turn it around and ask the questioner how long they reckon it will take, the answer is usually several hours, if not days.



 When sending details of your credit card always look to see if
When sending details of your credit card always look to see if  Consider using a browser with the
Consider using a browser with the  Exercise caution when downloading new apps. Only download apps from trusted sources such as
Exercise caution when downloading new apps. Only download apps from trusted sources such as 